The one constant across Chief Information Security Officers (CISOs) is that each of them have different expectations to live up to in their roles. While the role of CISO is still relatively new, companies haven’t yet embraced a consistent set of expectations for CISOs to deliver. Adding to the confusion, each CISO has different training and professional experiences that got them to their role. So, it’s easy to understand how these discrepancies could lead to misalignment and unclear messaging.
There is no clear roadmap for effective engagement or communication between security leaders and their business partners and peer executives. The way that security leaders communicate with their business partners in the boardroom and the way that business leaders engage with security increasingly suffer from unintended misunderstandings.
Being able to effectively deliver the right message, the right way, is one of the clearest ways to reduce risk and strengthen the value that cybersecurity brings to the whole organization.
Executives and CISOs need to speak BOTH cyber AND business
To illustrate a point, let’s broadly generalize the difference between cybersecurity and business professionals. Cybersecurity leaders are predominantly focused on technology tools, risks, system vulnerabilities and design interdependencies (possibly at the exclusion of business context). Business leaders are predominantly focused on operational processes and revenue growth (possibly at the exclusion of considering information risk). For each to do their job well, they NEED to tap into each other’s core strengths and focus areas.
So, how do we bridge the gap between cyber and business executives to deliver better outcomes?
Good managers are often described as being good teachers. They take the time to explain the principles to their staff. Yet, when put in a room of their peers, these same executives are less likely to invest the time to provide the relevant (and often necessary) context to benefit from the diversity of experience and expertise around the board room.
Cybersecurity is complicated, technical and requires business context to appropriately assess risk and prioritize resources. As executives, we have a responsibility to our stakeholders to get it ‘right’ and that starts with translating cybersecurity concepts and principles to our business partners, and explaining our business to our security teams. Just because we may be in a rush or dealing with a crisis doesn’t give us a pass to speak in ‘code.’
- If you’re in the room, you belong there. If you’re sitting around the boardroom table, you have an equal responsibility to identify and correct potential communication misalignment between security and business.
- Ask your colleague to “use more words.” Sometimes, the problem isn’t that we don’t understand, it’s that we need more context and description to see the point that is being made. This expression is an easy and non-threatening way to get additional context and information even if you don’t know specifically what to ask for.
- Expect questions or ask questions. This is a two way street. If you’re the listener and you’re not sure that you understand, ask clarifying questions. And if you are the speaker and aren’t getting signs of active listening from your audience ask THEM questions.
For the CISO: Know how to most effectively message to your stakeholders
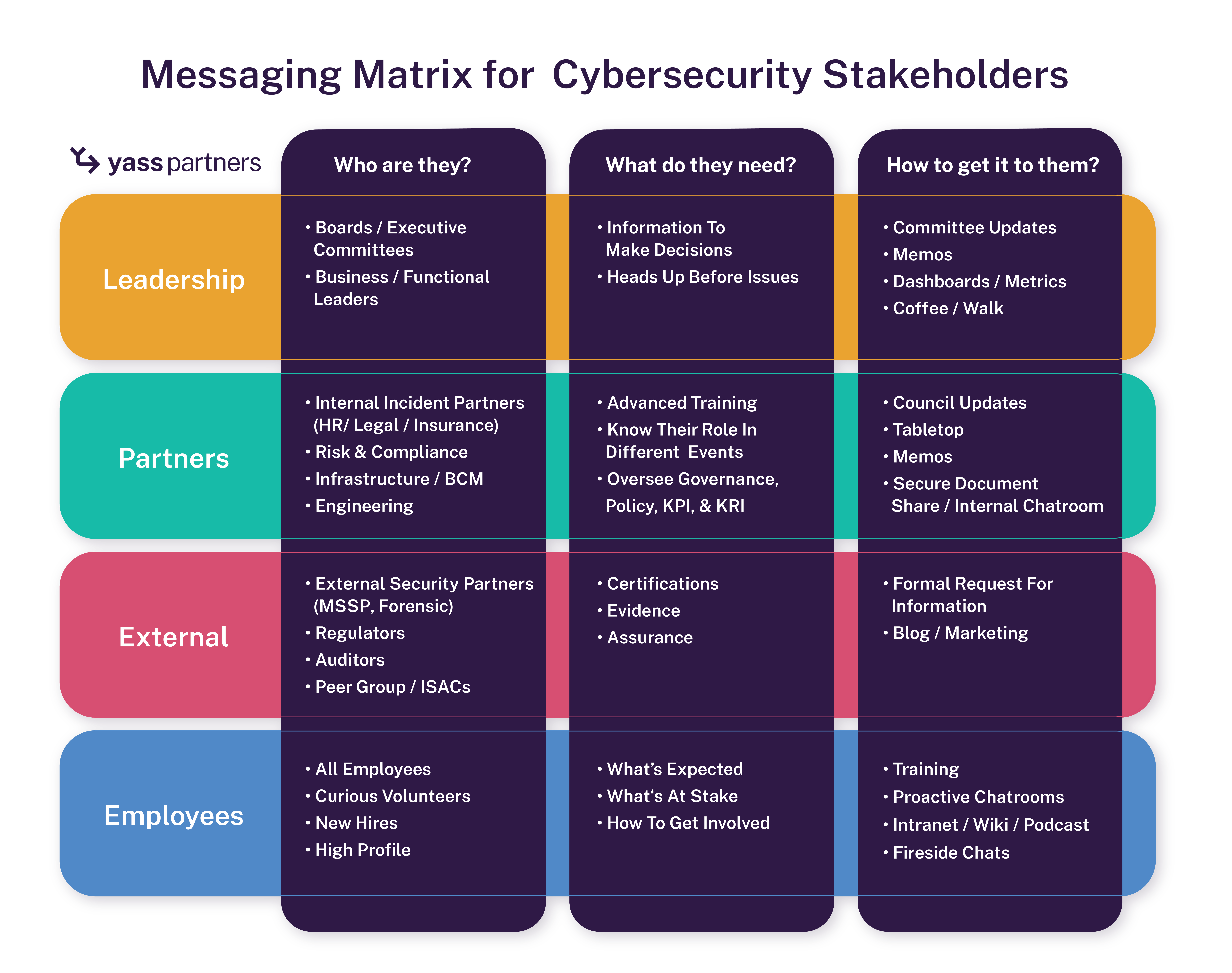
Security leaders have interactions with diverse stakeholders who have varying needs. Delivering all the messages to all the users without considering each of their styles or needs generally means that few, if any, of the stakeholders get what they actually need.
Engagement should be purpose-driven. The message should have a purpose that connects for each recipient. It’s equally as important to know what to message as it is to find the right time and format to deliver that message.
In security, understanding who your stakeholders are, what they need to know, and how to best get it to them is the fastest way to effective communication. The chart below is a reference and starting point.