Effective communication about cybersecurity is an increasing and layered challenge for CISOs, security leaders, communications professionals, business executives and boards.
CISOs are mission driven, focused on securing and defending. Anything that is not directly related to securing or defending may get deprioritized. So, serving up actionable impactful and behavior changing communications doesn’t always take top billing for security leaders as they simply don’t have the time.
What if there was a way to deliver more effective messages to the diverse stakeholders of security — executives, board directors, clients, partners — where we could also measure effectiveness, improve engagement and leverage the skillset and training cybersecurity practitioners already have?
CISOs should be leveraging their security training, in anticipating and reacting to social engineering and psychological operations, to become more effective communicators.
First, let’s review some foundational concepts
Cybersecurity is vast and intricate. The field that we call “cybersecurity” includes many different domains and functions. Frequently it means different things depending on the audience or industry.
- One of the areas that practitioners train in is to think about the threat vectors and attack surface while considering the motivation of criminals. It’s dirty work.
- Being able to think like the adversary is one way that cybersecurity controls are hardened.
- However, the same conditioning sometimes means that security practitioners unnecessarily constrain their communications. Sometimes, being too precise and too direct can impede effective communications.
People connect with things that matter to them. Cybersecurity is something that matters to individuals, corporations and government agencies equally.
- Cybersecurity is privacy, it’s safety, it’s financial, it’s trust. It’s something that carries weight and has purpose and meaning for individuals as well as organizations.
Different communities will engage with and process information differently. Understanding the different stakeholders and their frames of reference improves our ability to connect with them.
- Unconscious bias is real and unavoidable. The environment that we grew up in, our education, our values, and our experiences all contribute to shaping the lens through which we experience life and process information.
- Understanding the lens through which your stakeholders will experience and process information should inform how it is delivered.
Doing good is trendy. Brands have recognized that consumers want to put their money and support behind organizations that are committed to making the world a little bit better than when they got there.
- As we continue to increase our dependence on technology, companies will distinguish themselves by being responsible stewards of our data, privacy, and security.
- Recognizing this as a competitive differentiator and sharing that message will resonate with other executives outside of the security function to help build trust and increase engagement, possibly even with clients, industry partners and investors.
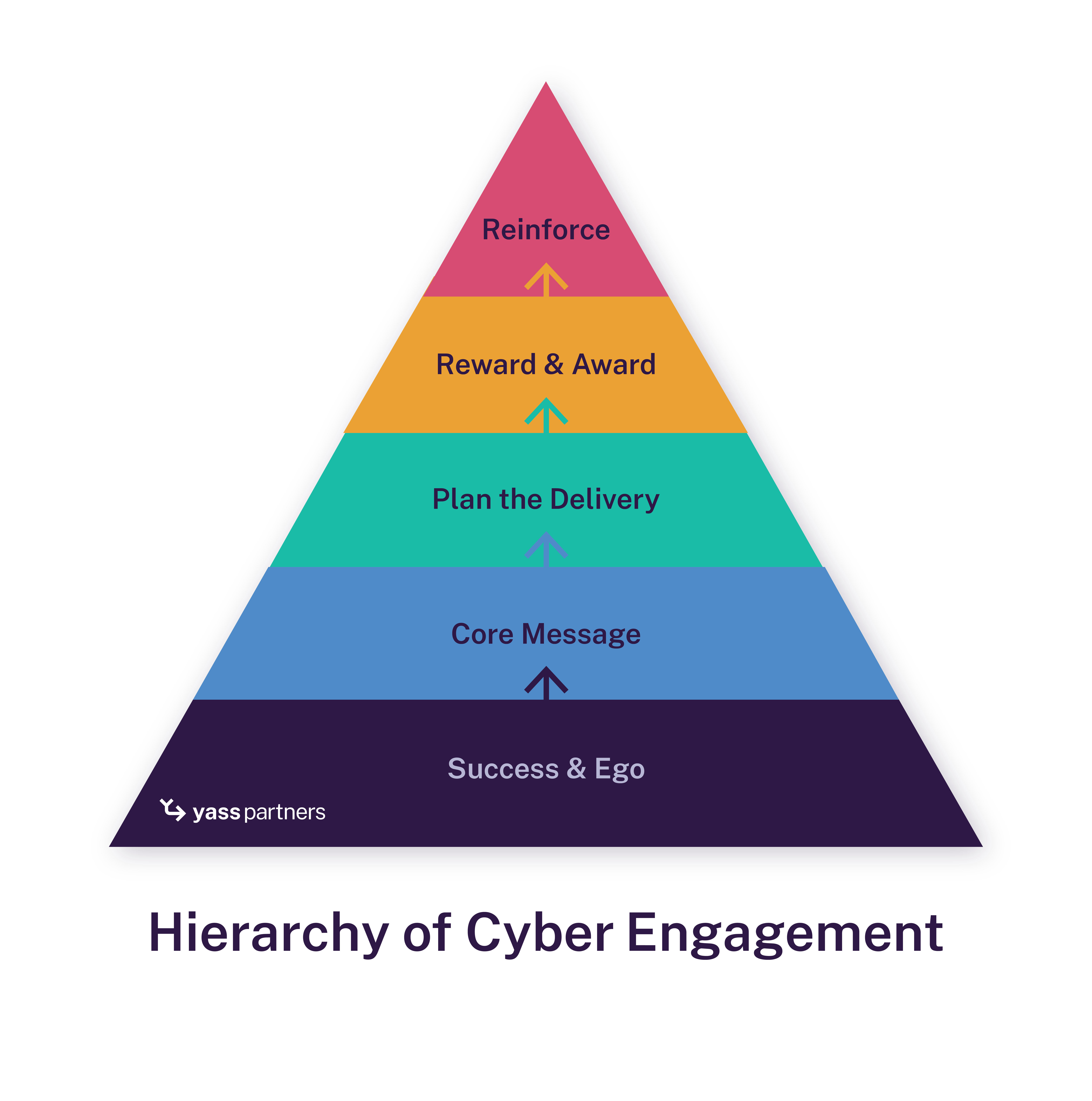
Hierarchy of Cyber Engagement Explained
Every great communicator, and even the not so great communicators, will remind us that we need to “know our audience” when preparing a message. But what do we actually need to know about our audience? And how do we use that knowledge to prepare the message for the greatest success and impact? Let’s apply the principles used in Psychological Operations and Social Engineering to more effectively craft and execute a message to deliver measurable impact and active engagement. In this hierarchy of cyber engagement, we go a step further by defining what motivates people to take action and to have an ownership stake in the ongoing results.